Rethinking IT Security: Logs That Don't Lie.
Blockchain timestamping shields your security logs, pipelines, and events from tampering—externally verified, provable, and audit-ready.


Why Your Logs Are a Liability
Cyberattacks start with the logs. Without external verification, your forensics are vulnerable—and every audit is a gamble.
What Security Teams Demand Today
Immutable Security Logs
Logs must remain untouchable, even during a breach.
Ironclad Chains of Evidence
Who did what—and when? Provability with zero blind spots.
Auditable CI/CD Pipelines
Builds, deployments, and releases must stay traceable.
External Integrity Layer
Internal systems are vulnerable. External proof is not.
Painless Compliance
Demonstrably meet ISO 27001, SOC2 & co.—without the overhead.

The Real Risk
When logs are tampered with, you lose the truth—and any chance of clean forensics.
Log Tampering
Attackers hit the logs first. Without external verification, nothing is secure.
Forensics Without Proof
Incomplete log histories render any analysis worthless.
Insecure CI/CD Pipelines
Without tamper-proof documentation, manipulations go undetected.
Audit Hell
ISO 27001 & SOC2 become a constant battle without external proof.
Centralized Attack Surfaces
Internal systems can be compromised. External ones can't.
Lack of Trust Foundation
Without proof of integrity, there's no foundation for security automation.
How Our Solution Works
External, immutable integrity—the perfect foundation for Security & DevOps.
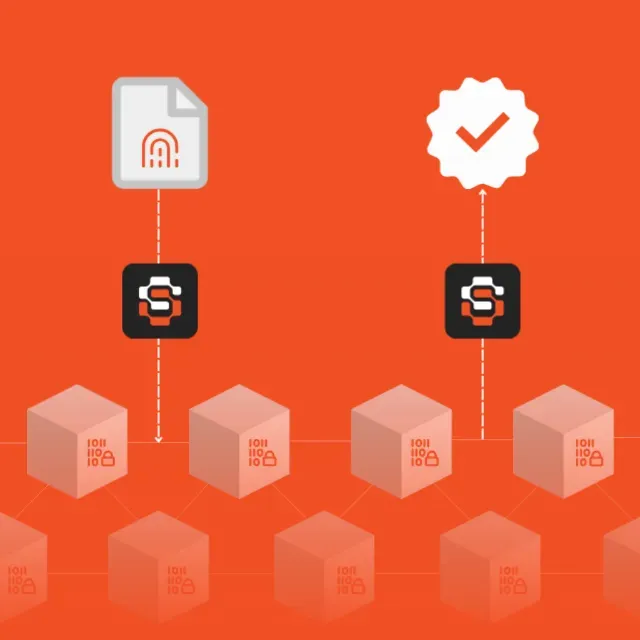
How It Works

Hash Every Log Entry
Every line gets an immutable identity.

Anchored on Bitcoin & Ethereum
Evidentiary power at the highest global security standard.

Immutable Process History
Pipelines, deployments, events—all auditable.

External Verification
Independent, neutral, and verifiable anytime.
Use Cases
Ideal for teams that demand uncompromising integrity and reliable forensics.
Security Logging & SIEM
Security Logging & SIEM
Logs become immutable and externally verified—perfect against log tampering.
Security Logging & SIEM
Logs become immutable and externally verified—perfect against log tampering.

Incident Response & Forensics
Incident Response & Forensics
Clear, provable chronologies for rapid analysis.
Incident Response & Forensics
Clear, provable chronologies for rapid analysis.
CI/CD Pipelines
CI/CD Pipelines
Builds, deployments, and releases documented with full transparency.
CI/CD Pipelines
Builds, deployments, and releases documented with full transparency.
Your Advantages
More security, less effort, undeniable proof.
Tamper-Proof Logs
Every entry is immutable—even on compromised systems.
Effortless Audit-Readiness
ISO 27001, SOC2, and other proofs, instantly available.
DevOps-Ready API
Easily integrates with GitLab, Jenkins, GitHub, Argo & co.
Proof in Seconds
Perfect for forensics, security automation, and Zero-Trust.


Proof That Counts
IPBee is committed to our clients' brand security, whether on marketplaces, domains, or social networks. Through our partnership with OriginStamp, we create global, secure proof for all copyrights.
Jan F. TimmeCEO, IPBee
The Future of IT Integrity
Why tamper-proof logs are the new security standard—and how blockchain timestamping is revolutionizing forensics, DevOps, and audits.
IT Security That Holds Up
In 15 minutes, we'll show you how blockchain timestamping makes your logs, pipelines, and forensics immutable.




