Forensic-Grade Security. Tampering is not an option.
With OriginStamp, you lock down mission-critical data, logs, and actions against tampering—forged-proof and anchored on Bitcoin and Ethereum. Immutable evidence for your security infrastructure. We invented blockchain timestamping in 2013. Period.


Why CISOs Rely on OriginStamp
Zero Trust demands immutable data. If your logs can be altered, your analysis is worthless and your forensics are compromised. OriginStamp delivers the integrity layer you can actually trust when everything is on the line.
What Modern Security Demands
Immutable Logs, Not Blind Trust
Every critical log entry gets a tamper-proof timestamp anchor. This is how you build a real Zero-Trust architecture.
Forensic-Grade Traceability
From the first access to the final command: every action remains technically provable and externally verifiable. No exceptions.
Trust Anchor for SIEM & Monitoring
SIEM events and alerts get an extra layer of integrity proof. Your analysis is now built on hard facts, not assumptions.
Regulatory Certainty for KRITIS & NIS2
Standardized proofs support ISO, KRITIS, and NIS2 requirements—without cluttering your SOC with new tools.
Integrity Without the Blockchain Overhead
Your systems stay as they are. We deliver the proof via global public blockchains. No vendor lock-in. Ever.
The Pain Points of a CISO
The real question is: in an incident, will your data become a weapon against you, or your strongest line of defense?
Tampered Logs Kill Every Analysis
Without integrity proof, any log entry can be disputed. OriginStamp makes log data provably unaltered, secured line by line.
Insiders Can Cover Their Tracks
Anyone with system privileges can often erase their footprints. With externally anchored hashes, every critical action remains technically provable.
Post-Breach, You Lack Court-Ready Evidence
If logs are alterable, forensic investigations fail in court. Blockchain timestamps create independent, rock-solid evidence.
Regulatory Pressure is Mounting
NIS2, KRITIS, ISO—they all demand tamper-proof evidence. OriginStamp delivers standardized, auditable proof for your security processes.
Security Tools Operate in Silos
SIEM, IAM, OT monitoring—multiple data sources, but no unified chain of evidence. Timestamping becomes the common trust anchor in your stack.
Lack of Integrity Proof Puts the Company at Risk
Without immutable data points, every incident becomes a liability nightmare. With OriginStamp, you turn the tables—data becomes your shield.
The Technology
Simply put: Hash, anchor, verify. No trust required—just math. And that's exactly what auditors, investigators, and forensic experts love.
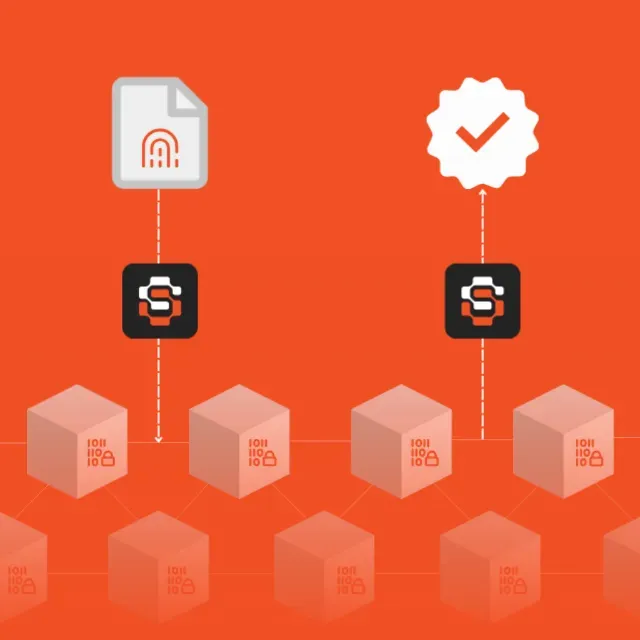
How It Works

Hash
Only the hash leaves your system. Logs, events, and data remain entirely within your infrastructure—perfect for sensitive critical environments.

Anchor
The hash is anchored on Bitcoin or Ethereum—globally visible, immutable, and independent of your security stack.

Verify
Any auditor, investigator, or analyst can independently verify the integrity and timestamp of the data at any time—without ever needing to ask us.

No Trust—Just Math
No black box, no vendor hype. Cryptography and public ledgers are the arbiters of truth, not some manufacturer's marketing slide.
Use Cases for CISOs
For industry, energy providers, critical infrastructure, scanning services, banks, and anyone for whom tampering is not an option.
Tamper-Proof Log Files
Tamper-Proof Log Files
Server, security, and network logs get a blockchain timestamp. The result: forensic-grade records that will survive any audit.
Tamper-Proof Log Files
Server, security, and network logs get a blockchain timestamp. The result: forensic-grade records that will survive any audit.

Securing Critical Infrastructure
Securing Critical Infrastructure
Access controls, system commands, camera data—everything is documented immutably. Perfect for energy, manufacturing, and critical infrastructure.
Securing Critical Infrastructure
Access controls, system commands, camera data—everything is documented immutably. Perfect for energy, manufacturing, and critical infrastructure.
Monitoring & SIEM Trust Anchor
Monitoring & SIEM Trust Anchor
SIEM events and alerts get an additional integrity layer. Every alert chain remains traceable and tamper-proof during incident response.
Monitoring & SIEM Trust Anchor
SIEM events and alerts get an additional integrity layer. Every alert chain remains traceable and tamper-proof during incident response.
Your Advantage
What OriginStamp means for your security infrastructure: less guesswork, more proof. Fewer excuses, more facts.
Forensic-Grade Logs & Data
Immutable, globally verifiable proof for logs, events, and system actions—auditable for decades, even after the systems are long gone.
Zero-Trust-Ready Security Architecture
Integrity becomes a core component of your Zero-Trust strategy. Every critical action gets independent, cryptographic proof.
API-First, No Tool Sprawl
OriginStamp integrates via API into your existing SIEM, IAM, and monitoring solutions. You enhance your stack, you don't add another one to manage.
No Additional Infrastructure
No private blockchain, no new servers, no overhead. You use public ledgers as your security anchor—we handle the rest.


Proof That Matters
IPBee is committed to protecting our clients' brand integrity across marketplaces, domains, and social networks. Our partnership with OriginStamp allows us to create global, secure proof of all copyrights.
Jan F. TimmeCEO, IPBee GmbH
Blog Articles for Security Leaders
Why logs without tamper-proof evidence are worthless, how Zero Trust closes the integrity gap, and the real role of immutable data in incident response.
Security Starts with Immutable Data
In 15 minutes, we'll show you how timestamping fortifies your security architecture, enhances forensics, and has your back when it counts.




